Risk Level: | Threat Name: | Backdoor.Prorat |
| Threat Family: | Backdoor | |
| Type: | Trojans | |
| Subtype: | Trojans | |
| Date Discovered: | ||
| Length: | Unknown | |
| Registry Clean-Up Tool: | Free Download |
ProRat download. ProRat is a Remote Administration Tool made by PRO Group. Download Review Comments (19) Questions & Answers (4) Download latest version from Software Informer. DOWNLOAD NOW 3.1 MB. See the report or download other versions of ProRat. Alternative software Radmin Viewer. Find related downloads to Prorat V1.9 freeware and softwares, download LastPass, CuteFTP, HDD Regenerator, Baidu PC Faster, 360 Total Security, 360 Internet Security for Mac, EasyMail Objects, Total C. Download PRORATv1.9 FREE- Kali ini saya akan membagikan software hacking yaitu 'ProRat'.Prorat adalah sebuah tool hacking yang luar biasa. Dan hampir 100% saat ini berhasil bekerja. Tool ini buatan orang Turki, berfungsi untuk menyusup ke komputer orang lain, melihat isinya bahkan memegang kendalinya. Nov 28, 2016 Free Virus Removal Tool for W32/Prorat Trojan is a lightweight and portable software application that scans the computer for the W32/Prorat Trojan and removes it if found.
Download Prorat Full Version
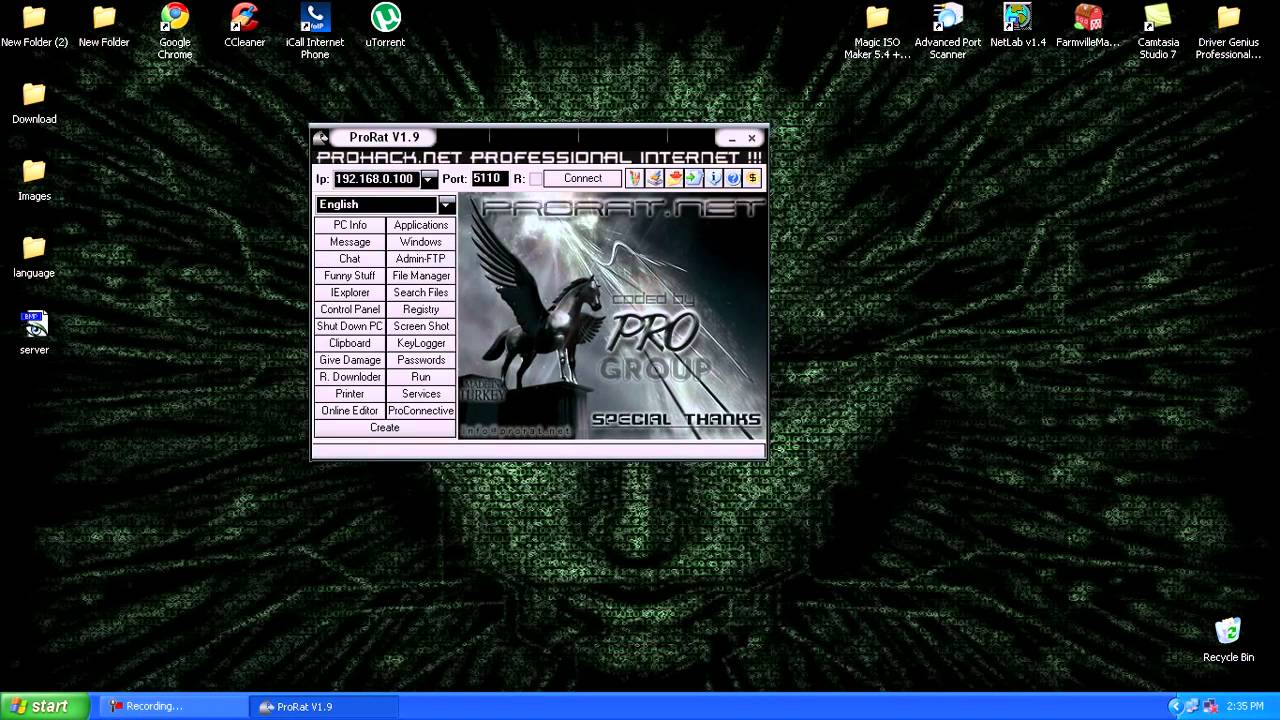
Download Prorat
Compatible with Windows 10, 8, 7, Vista and Windows XP
Optional Offer for WinThruster by Solvusoft | EULA | Privacy Policy | Terms | Uninstall
Download Prorat 64 Bit
What is Backdoor.Prorat?

Backdoor.Prorat is a trojan that comes hidden in malicious programs. Once you install the source (carrier) program, this trojan attempts to gain 'root' access (administrator level access) to your computer without your knowledge.

Trojans like Backdoor.Prorat are difficult to detect because they hide themselves by integrating into the operating system. Once it infects your computer, Backdoor.Prorat executes each time your computer boots and attempts to download and install other malicious files. Upon successful execution, it deletes the source program, making it more difficult to detect.
What are Trojans?
Trojans are one of the most dangerous and widely circulated strains of malware. A trojan disguises itself as a useful computer program and induces you to install it. By the time that you discover that the program is a rogue trojan and attempt to get rid of it, a lot of damage has already been done to your system.
The intent of a trojan is to disrupt the normal functionality of a computer, gradually stopping it from working altogether. Trojans can make genuine software programs behave erratically and slow down the operating system. Trojans can delete files, monitor your computer activities, or steal your confidential information. They can enable attackers to have full access to your computer… as if they are physically sitting in front of it.